I've been interviewing Ed White, manager of NXP's skilled help and Engineering capabilities, and Akshay Bhat, Director of Engineering, safety solutions at Timesys by way of electronic mail to find out greater about NXP Linux BSP building method, and how Timesys can help to hold it updated and comfortable with its Vigiles carrier.
Q1. CNX utility readers recently mentioned NXP Linux BSP update status. One adult especially referred to Linux 4.14.ninety eight used within the BSP was neatly over a yr ancient, and there were a number of opinions about the subject, together with one grownup suggesting NXP only provides a good BSP and it turned into the ultimate accountability of the consumer to merge Linux security patchsets. could you clarify the average development manner for NXP Linux BSP, and why the company selected not to replace the patchsets regularly?
reply: The kernel approach for NXP's i.MX family BSPs closely follows the annual cadence of kernel.org's LTS kernel selection. As soon as kernel.org establishes the next authentic LTS kernel edition, NXP transitions our inside building to that certain kernel. although, the migration of the kernel is only one point of our subsequent main release. There could be a couple of associated updates to be included, reminiscent of a new edition to Yocto, updates to U-Boot, and a lot of different package changes we integrate into the Yocto free up selected to the i.MX BSP. These components, plus our rigorous testing manner create an inevitable prolong between the neighborhood edition of the newest LTS kernel liberate and NXP's i.MX board help kit (BSP) according to that same kernel.
We should also agree with a number of other elements that come into play between our deliberate cadence of Linux LTS kernel updates. NXP may introduce new items, or there may be updates to a number of programs, and naturally, there are concern resolutions (including LTS minor edition updates) to be regarded. Our engineering crew ought to balance all these components while protecting constant nice necessities for the entire i.MX product family being supported by means of every BSP liberate.
We (NXP) supply assist for each new LTS kernel for at the least one (1) year after delivering the initial commonplace availability (GA) liberate of that version. From the exchange factors I just described, you'll be able to expect to look a few minor updates in between the primary LTS kernel version updates. These usually come as comprehensive BSP releases, and sometimes as a specific patch update. purchasers constructing i.MX-primarily based products should video display NXP.com to make certain they've the newest BSP release and updates.
I examine a dialogue from considered one of your readers about an NXP associate product launched in may of 2020 according to our L4.14.98 BSP. The dialogue implied NXP has not supplied a more latest Linux kernel version BSP for i.MX – which isn't authentic. on account that releasing the L4.14 kernel edition BSP, we now have delivered an L4.19 LTS kernel version BSP as well as a couple of minor version updates in-between. In late 2019 the building crew turned into already migrating to LTS kernel version L5.4, which became initially released via us in Q1, 2020.
In protection of any NXP partners or shoppers setting up items in keeping with i.MX items, they each have their personal development and verify cycles and usually opt for the NXP BSP version that suits their production schedule and desires. despite having a product "officially" developed on a particular NXP BSP kernel edition does not imply they haven't been monitoring their BSP for the latest vulnerabilities and making use of the applicable updates. Let's discuss how NXP is enabling the means to have the newest and most comfy SW platform – with out a wholesale BSP replace – by using the Vigiles device powered with the aid of Timesys.
Q2. quickly after this discussion, I found out Timesys Vigiles carrier that makes bound the Linux BSP is cozy with the customer's own patches. might you provide an outline of the building workflow?
reply: NXP/Timesys has two offerings to support retain machine security:
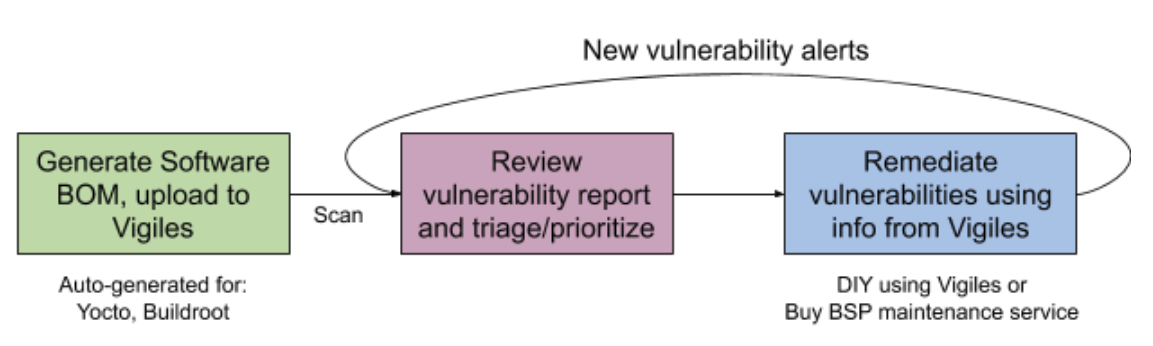
 click on to magnify
click on to magnifybe aware: Vigiles is pre-integrated in NXP i.MX Yocto BSP releases. valued clientele can register for a Vigiles top 30-day evaluation to adventure all the points of the tool in thei r own challenge. (After 30 days, it converts to a much less function-prosperous, free version.) See sample demo report.
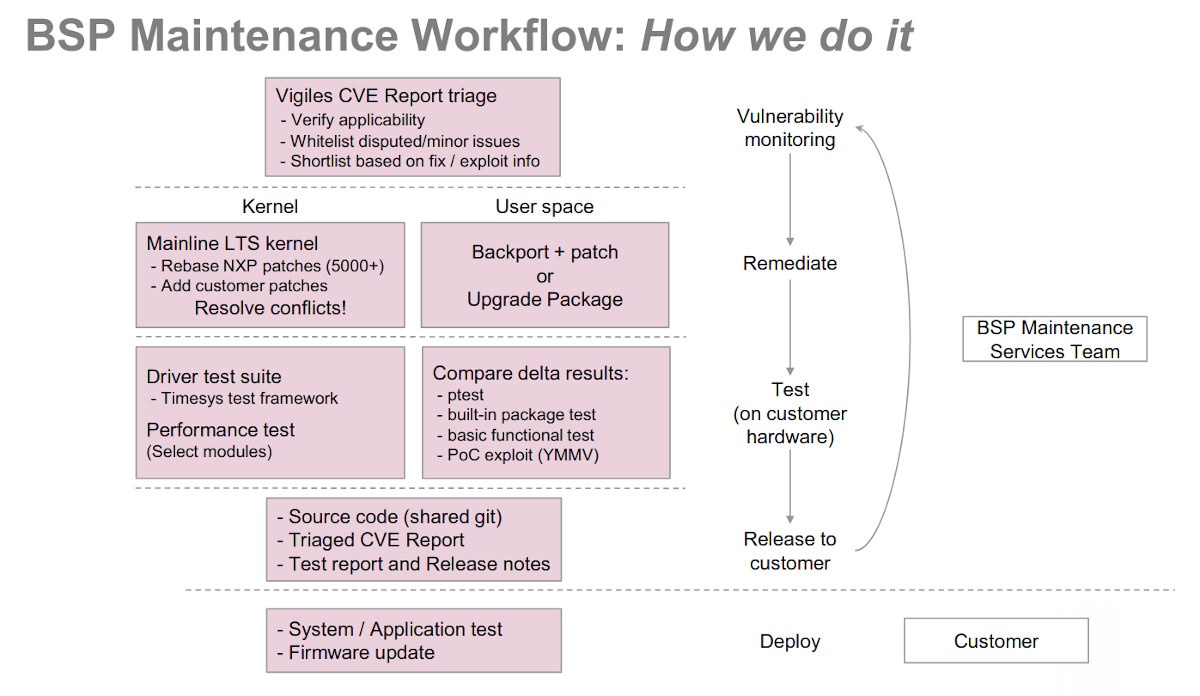
 BSP upkeep Workflow – source: Lifecycle upkeep of Your BSP presentation slides
BSP upkeep Workflow – source: Lifecycle upkeep of Your BSP presentation slidesgreater about the technique answered beneath this autumn, BSP upkeep part.
Q3. New CVE (average Vulnerabilities and Exposures) get discovered day by day, so the system must be updated always to be saved comfortable. How commonly does a product managed via Vigiles usually get safety updates?
reply:
this fall. Some open-source equipment, together with the Yocto mission, include CVE checkers. That means some shoppers could practice the newest Linux patches for Linux 4.14.xxx and run a CVE checker to discover competencies vulnerabilities themselves. Would Vigiles still make feel if that's the case? What would be the delivered merits of the offer?
reply: sure, the Vigiles and BSP upkeep capabilities nevertheless make experience for purchasers such as you are describing.
Our Vigiles capabilities give significantly greater correct and timely vulnerability data and greater accurate utility component evaluation than open-supply CVE checkers, which dramatically cuts evaluation and mitigation time. Our services additionally consist of the collaboration, mitigation, and update tools and features that are crucial for a good safety and preservation procedure. These are based mostly in tremendous half on trade most effective practices derived from heaps of utility projects we now have supported over the years, all at a really competitively priced.
whereas Vigiles presents the above benefits over open-supply CVE checkers to in the reduction of the burden in accurately monitoring and discovering fixes, there remains effort/skill required for patching, resolving conflicts, and trying out. hence, consumers may wish to go together with the managed BSP preservation carrier to absolutely offload the BSP protection renovation burden to NXP/Timesys. this could give large can charge reductions and outcome in a more at ease BSP.
somebody taking a DIY approach with open-supply CVE checkers can definitely try to recreate that and reinvent the wheel, but it surely would now not make sense to do so.
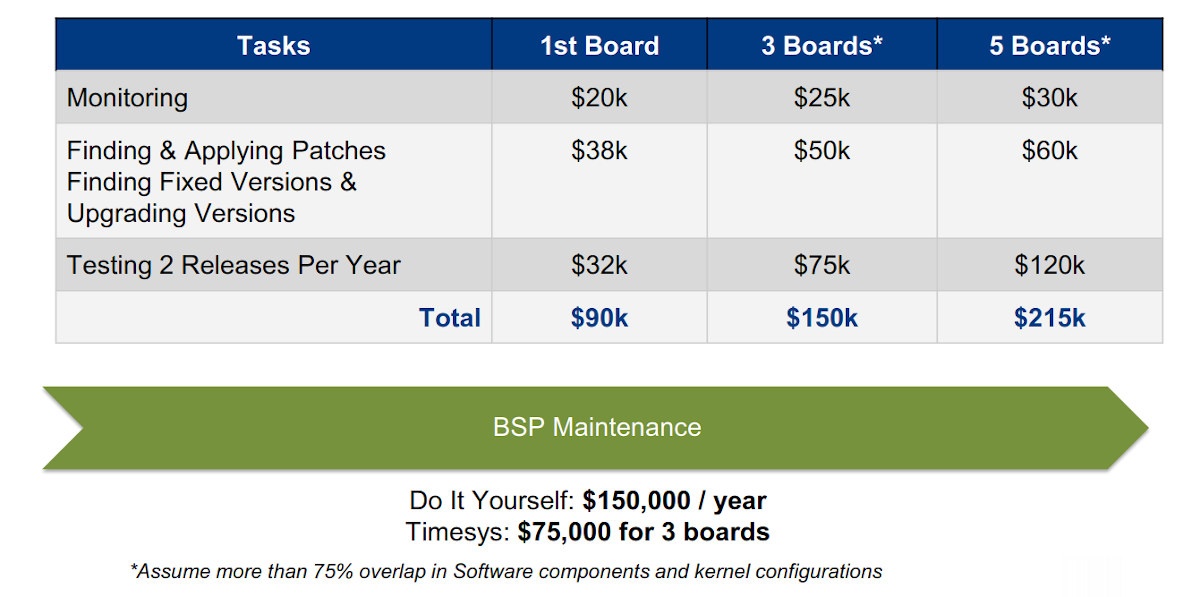
 Estimation of BSP upkeep charges per Board
Estimation of BSP upkeep charges per BoardTo supply specifics about these added advantages:
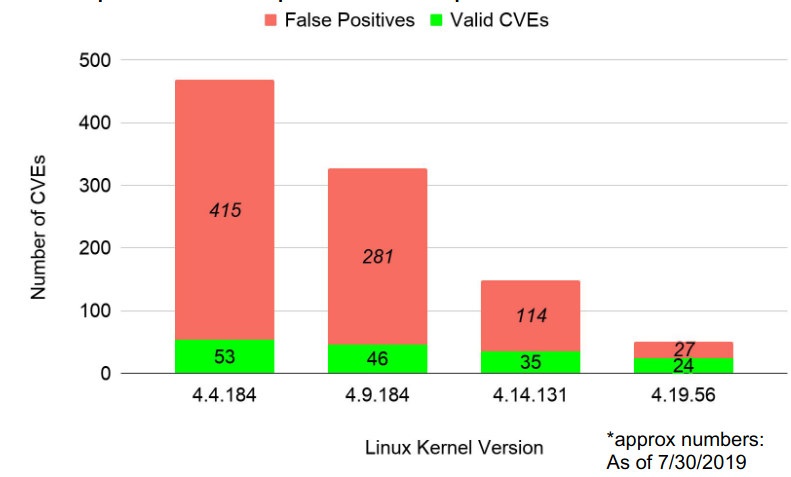
 Vigiles pulls vulnerability records from distinct sources such as NVD and security Bulletins (Ubuntu, Debian), which is run via in-house-developed curation algorithms to reduce false positives (by way of pass-verifying obtainable fixes in opposition t git commits to verify affected version tiers, and so forth.), map vulnerabilities to kit config alternatives and limit to affected structures. in addition, the Timesys safety research crew manually screens vulnerabilities in programs from construct systems corresponding to Yocto and Buildroot, SoC vendor advisories, and mailing lists similar to oss-security, and provides/curates vulnerability suggestions as essential. All of those steps result in stronger accuracy and insurance while reducing false positives in our curated database (as much as forty% growth over NVD for definite packages).
Vigiles pulls vulnerability records from distinct sources such as NVD and security Bulletins (Ubuntu, Debian), which is run via in-house-developed curation algorithms to reduce false positives (by way of pass-verifying obtainable fixes in opposition t git commits to verify affected version tiers, and so forth.), map vulnerabilities to kit config alternatives and limit to affected structures. in addition, the Timesys safety research crew manually screens vulnerabilities in programs from construct systems corresponding to Yocto and Buildroot, SoC vendor advisories, and mailing lists similar to oss-security, and provides/curates vulnerability suggestions as essential. All of those steps result in stronger accuracy and insurance while reducing false positives in our curated database (as much as forty% growth over NVD for definite packages).Vigiles is more than a monitoring tool, it provides an conclusion-to-conclusion workflow to tackle vulnerabilities at volume. This allows for a tool maker to enhance product security at a enormously reduce can charge than trying to DIY with open source CVE checkers.
Having the right tools, automation and advantage is essential to bringing the cost of BSP preservation down and reducing protection chance. in brief, NXP/Timesys capabilities seize business most excellent practices to support bring greater at ease items with reduced maintenance cost permitting end purchasers to focal point on product cost add.
Q5. Vigiles is certainly targeted at NXP Linux BSP, but what about different SoCs with mainline Linux aid or a BSP with a Linux LTS kernel? Would you be in a position to supply aid? in that case, would the silicon dealer need to be worried, or any client could rent your functions for support?
answer: For NXP BSPs, Vigiles and/or BSP renovation can be purchased at once via NXP.
For other carriers' BSPs, Vigiles and/or BSP upkeep will also be purchased through Timesys. The silicon seller does not need to be concerned, despite the fact Timesys has longstanding relationships with many carriers. Any end-client can appoint Timesys for his or her specific protection or BSP protection wants. Timesys has capabilities in preserving BSPs on a variety of SoCs. further, if an end-consumer is not on an LTS kernel, Timesys can first migrate them to an LTS edition below an further service contract and then delivery BSP renovation to keep the device secure.
Biography of interviewees
Jean-Luc all started CNX software in 2010 as a component-time exercise, before quitting his job as a utility engineering supervisor, and starting to write daily news, and studies full time later in 2011.
No comments:
Post a Comment